Top Choice for Canadian Immigration Services
We are a Canadian immigration firm providing wide range of immigration services. We have a proven track record of successfully handling complex cases.





Our Services
DragonX Offensive Securities is a cybersecurity service company specializing in advanced threat detection, penetration testing, and vulnerability assessments. We offer tailored offensive security solutions to protect businesses from emerging cyber threats and safeguard critical digital assets.

Incident Response and Recovery
In the event of a security incident, our rapid response team is on standby to mitigate the impact and restore normal operations swiftly.
Learn more
Security Consulting and Compliance
Our experts provide guidance and support to ensure that your organization remains compliant with industry regulations and standards.
Learn more
Vulnerability Assessments and Penetration Testing
We identify and address vulnerabilities in your systems through comprehensive assessments and penetration testing.
Learn more
Threat Detection and Prevention
Utilizing advanced technologies and threat intelligence, we detect and neutralize cyber threats before they can breach your defenses
Learn moreOur Success Stories: Inspiring Case Studies of Canada Immigration
Don't hesitate to contact us about any question you might be interested in



Why Choose us?
Experience unmatched expertise and personalized guidance for your seamless Canadian immigration journey!
Streamlined Process
Our easy steps will give you a seamless immigration application experience.
Client Top Choice
Our services are focused on client satisfaction which leads to 90% of our business growth through client referrals
Licensed Team
Our team comprises experienced immigration professionals who are certified by Canadian Immigration Regulatory bodies
Personal Case Manager
We ensure a hassle free immigration experience by assigning dedicated immigration case experts to handle your immigration process
Custom Dashboard
We believe in open and transparent communication with you, ensuring you have your own easy to navigate dashboard on our portal to be informed about every update in your immigration case.
Success Rate
Our track record of successful immigration cases speaks for itself. We have an impeccable track record of successfully doing the most complex cases.
Comprehensive Range of Services
We offer a comprehensive suite of services to address various immigration needs for individuals, families, Businesses, and many more.
Personalized Immigration Solutions
We understand that each client's immigration journey is unique, which is why we take a personalized approach to tailor our services to the specific needs and circumstances of each client.
Continued Support and Guidance
Our commitment to our clients doesn't end with the successful completion of their immigration case. We provide ongoing support and guidance to help clients settle into their new life in Canada successfully.
Comprehensive Range of Services
We offer a comprehensive suite of services to address various immigration needs for individuals, families, Businesses, and many more.
Personalized Immigration Solutions
We understand that each client's immigration journey is unique, which is why we take a personalized approach to tailor our services to the specific needs and circumstances of each client.
Continued Support and Guidance
Our commitment to our clients doesn't end with the successful completion of their immigration case. We provide ongoing support and guidance to help clients settle into their new life in Canada successfully.
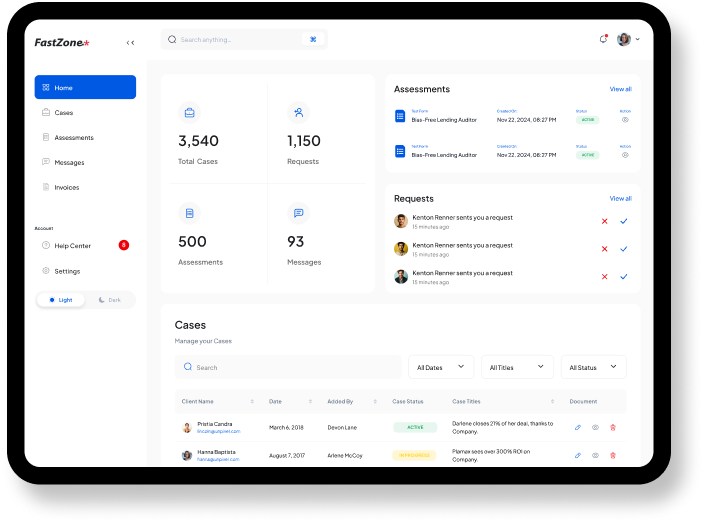
Manage Your Immigration Cases Effortlessly
Easily access and manage all your immigration cases in one place. Our user-friendly dashboard allows you to track progress, receive updates, and ensure that nothing falls through the cracks
Defend Your Digital Domain with DragonX
Protect Your Business with Cutting-Edge Cybersecurity Solutions
Stay ahead of digital threats with our advanced cybersecurity services. We safeguard your data, ensure compliance, and provide 24/7 protection, so you can focus on growing your business with peace of mind

Free Website Hack Test
Is your website prone to hacking? check now.
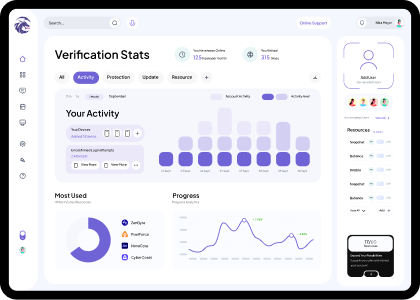
Our Cyber Security Services
We understand the critical importance of protecting your business, your data, and your reputation in an increasingly interconnected world.

Incident Response and Recovery

Security Consulting and Compliance

Vulnerability Assessments and Penetration Testing

Threat Detection and Prevention
Why choose us?
Choose DragonX for unparalleled cybersecurity services, blending cutting-edge technology with expert human intelligence to provide comprehensive protection against evolving digital threats

Proven Expertise

Proactive Defense

Tailored Solutions

24/7 Monitoring
Articles & Resources
Delve into the depths of cybersecurity with our curated insights, trends, and updates..

RomCom Group Leveraging Microsoft Office Zero-Day Vulnerability to Spread Ransomware
A zero-day vulnerability refers to a software flaw that is unknown to the software vendor and for which no official patch or fix exists at the time of ...
-
-
9th September, 2024

Top 10 Vulnerability Assessment Tools to Use in 2024
With the rapid increase in cyberattacks, data breaches, and evolving threat landscapes, vulnerability management has become a critical part of any cybe...
-
-
7th September, 2024

In-Depth Comparison: Quality Analyst vs. Penetration Tester
A penetration tester (often called a pentester) is focused on security testing. Their jo...
-
-
6th September, 2024
We do more than just providing security.
Through a holistic approach to cybersecurity, DragonX Offensive Securities partners with organizations to build resilience, foster innovation, and ensure a secure digital future.

Team Contests
Red team vs Blue team competitions simulate real-world cyber threats, fostering collaboration, and honing defensive and offensive cybersecurity skills

Attack Simulations
Proactively testing and refining cybersecurity measures through simulated cyberattacks to enhance preparedness and resilience

Bug Bounty Hunting
Harnessing the power of ethical hackers to uncover vulnerabilities and strengthen cybersecurity defenses
Trusted Tools that we use.
Latest News and Updates

BlackByte Ransomware Exploits...
The threat actors behind the...

CISA Flags Critical...
The U.S. Cybersecurity and Infrastructure...

New QR Code...
Cybersecurity researchers are calling attention...

PEAKLIGHT Downloader Deployed...
Cybersecurity researchers have uncovered a...

New Linux Malware...
Cybersecurity researchers have uncovered a...
Latest News
-

1
Posted Date Aug 28, 2024
BlackByte Ransomware Exploits...
The threat actors behind the...
-

2
Posted Date Aug 28, 2024
CISA Flags Critical...
The U.S. Cybersecurity and Infrastructure...
-

3
Posted Date Aug 28, 2024
New QR Code...
Cybersecurity researchers are calling attention...
-

4
Posted Date Aug 27, 2024
PEAKLIGHT Downloader Deployed...
Cybersecurity researchers have uncovered a...
-

5
Posted Date Aug 27, 2024
New Linux Malware...
Cybersecurity researchers have uncovered a...
Stay up to date with our news, ideas and updates
We utilize cookies on this website to distinguish you from other users for an enhanced experience and targeted advertising. Your continued use of this website implies your consent for us to use cookies. Please refer to our Cookie Policy. for more details
DragonX Cookie Policy
At DragonX, we employ cookies on our website to enhance the site, providing the best service and customer experience possible
Category
Necessary (Always active)
These cookies enable essential site features like secure log-in and consent preference adjustments, without storing any personally identifiable data
Functional
This category aids in specific functions such as sharing website content on social media platforms, receiving feedback, and incorporating third-party features
Analytics
Analytical cookies are utilized to comprehend visitor interactions on the website, offering insights into metrics like visitor numbers, bounce rates, and traffic sources
Performance
These cookies help in understanding and analyzing important performance indicators of the website to enhance the user experience
Advertisement
Tailored advertisements are provided to visitors based on previously visited pages, while also evaluating the effectiveness of ad campaigns









