We wanted to gauge how much professionals know about the different cybersecurity teams. The results of our poll on who is responsible for constructing an organization's cybersecurity system were surprising. The responses were evenly split between Blue and Yellow. The correct answer is Yellow, and we'll explain why in the following write-up.
Colors play an essential role in our lives. In school, when we ran out of a particular color, we would mix primary colors to create new ones. In cybersecurity, teams are also named after colors, each representing their specific tasks.
Let's explore how teams are organized in a cybersecurity environment and what Red, Blue, Yellow, Purple, Green, and Orange signify.
Here is the rationale behind the color naming system.
Primary Colors: Red, Blue, Yellow
Secondary Colors: Purple, Green, Orange
By mixing any two primary colors, we get secondary colors. Similarly, combining primary teams results in secondary teams.
Let's break it down one by one.
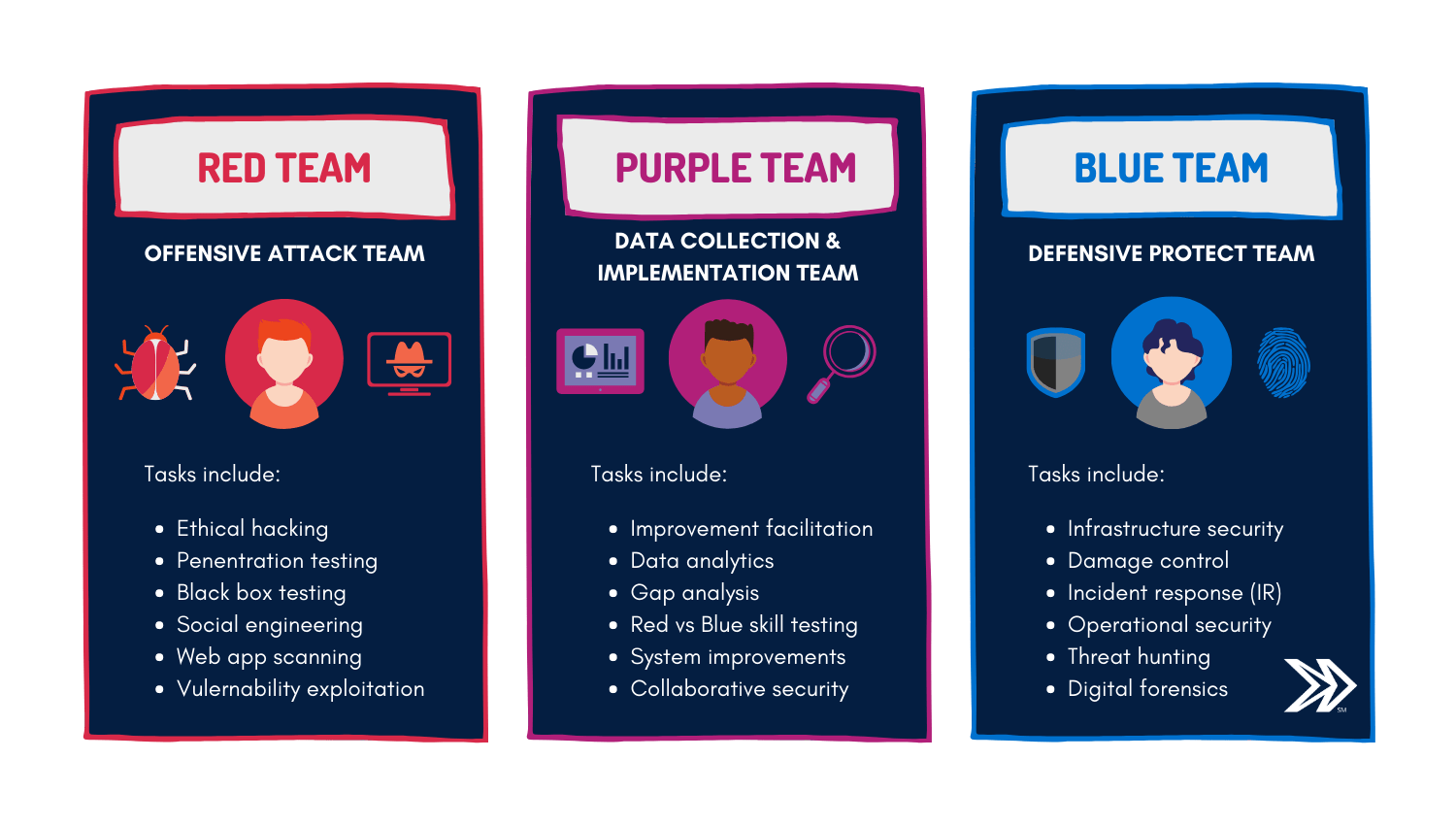
**Red Team**
The Red Team handles offensive testing. They simulate real-world attacks, acting like adversaries to test the system's defenses. Red Team operations are most effective when conducted by external cybersecurity firms.
Here’s a simple scenario of how the Red Team operates:
Only the top management knows about an impending Red Team operation. The team might enter the premises disguised as job candidates, pest control, or cleaning staff, much like spies in movies.
They identify security loopholes and vulnerabilities, such as the number of security cameras, exit routes, fire alarm accessibility, and guard deployment. This process can take from 30 days to several months. The Red Team analyzes behavior and strategizes attacks.
Note: Only top management is aware of Red Team operations.
After exploiting vulnerabilities, they compile a comprehensive report and present it to the company.
Their tasks include:
- Offensive security
- Ethical hacking
- Exploiting vulnerabilities
- Penetration testing
- Blackbox testing
- Social engineering
- Web application scanning
The Red Team uses all possible methods to conduct their operations without boundaries.
**Blue Team**
The Blue Team is responsible for defense. They protect sensitive data and ensure the security infrastructure is robust.
Their tasks include:
- Defensive security
- Infrastructure protection
- Damage control
- Incident response
- Operational security
- Threat hunting
- Digital forensics
Note: Large enterprises may have thousands of Blue Team members handling various defensive functions.
**Purple Team**
The Purple Team enhances the performance of both the Red and Blue Teams.
They improve detection and defense capabilities, streamline operations, and enhance overall attack and defense outcomes.
**Orange Team**
The Orange Team helps developers adopt an attacker’s mindset by providing real-time information from the Red Team.
They play a crucial role in developing secure, error-free, and bug-free applications, similar to how a locksmith knows how to break locks to create better ones.
**Yellow Team**
Also known as “builders,” the Yellow Team is responsible for developing secure software and applications. They collaborate with Research and Development to improve security features.
Yellow Team members include:
- Software developers
- Application developers
- Software engineers
They use insights from both the Red and Blue Teams to enhance their output.
**White Team**
The White Team acts as a referee between the Red and Blue Teams, ensuring fair play.
They oversee Red Team operations, analyze compliance, and manage logistics and hardware. During unplanned Red Team operations, they observe Blue Team performance.
**Green Team**
The Green Team bridges the gap between the Blue and Yellow Teams. They educate the Yellow Team on real-time security issues and inform the Blue Team about software frameworks and dependencies.
The Green Team plays a crucial role in ensuring both teams work together effectively for better outcomes.
Latest News and Updates
Latest News
-

1
Posted Date Aug 28, 2024
BlackByte Ransomware Exploits...
The threat actors behind the...
-

2
Posted Date Aug 28, 2024
CISA Flags Critical...
The U.S. Cybersecurity and Infrastructure...
-

3
Posted Date Aug 28, 2024
New QR Code...
Cybersecurity researchers are calling attention...
-

4
Posted Date Aug 27, 2024
PEAKLIGHT Downloader Deployed...
Cybersecurity researchers have uncovered a...
-

5
Posted Date Aug 27, 2024
New Linux Malware...
Cybersecurity researchers have uncovered a...